Do You Know What’s in Your Supply Chain? The Case for Better Security
I recently read an interesting report by CyCognito on the top 3 vulnerabilities on third-party products and it sparked my interest to reexamine the supply chain risks in software engineering. This article is an attempt at that.

The Vulnerability Trifecta in Third-Party Products
The CyCognito report identifies three critical areas where third-party products introduce significant vulnerabilities:
- Web Servers
These foundational systems host countless applications but are frequently exploited due to misconfigurations or outdated software. According to the report, 34% of severe security issues are tied to web server environments like Apache, NGINX, and Microsoft IIS. Vulnerabilities like directory traversal or improper access control can serve as gateways for attackers. - Cryptographic Protocols
Secure communication relies on cryptographic protocols like TLS and HTTPS. Yet, 15% of severe vulnerabilities target these mechanisms. For instance, misconfigurations, weak ciphers, or reliance on deprecated standards expose sensitive data, with inadequate encryption ranking second on OWASP’s Top 10 security threats. - Web Interfaces Handling PII
Applications that process PII—such as invoices or financial statements—are among the most sensitive assets. Alarmingly, only half of such interfaces are protected by Web Application Firewalls (WAFs), leaving them vulnerable to injection attacks, session hijacking, or data leakage.
Beyond Web Servers: The Hidden Dependency Risks
You control your software stack, but do you actually know what runs beneath those flashy Web/Application servers?
Drawing parallels from my previous article on PyPI and NPM vulnerabilities, it’s clear that open-source dependencies amplify these threats. Attackers exploit the very trust inherent in supply chains, introducing malicious packages or exploiting insecure libraries.
For example:
- Attackers have embedded malware into popular NPM and PyPI packages, which are then unknowingly incorporated into enterprise-grade software.
- Dependency confusion attacks exploit naming conventions to inject malicious packages into CI/CD pipelines.
These risks share a core vulnerability with traditional third-party systems: an opaque supply chain with minimal oversight. This is compounded by the ever-decreasing cycle-times for each software releases, giving little to no time for even great Software Engineering teams to doa decent audit and look into the dependency graph of the packages they are building their new, shiny/pointy things that is to transform the world.
Why Software Supply Chain Attacks Persist
As highlighted by Scientific Computing World, software supply chain attacks persist for several reasons:
- Aggressive GTM Timelines: Most organisations now run quarterly or even monthly product roadmaps, so it is possible to launch a new SaaS product in a matter of days to weeks by leveraging other IaaS, PaaS or SaaS systems – in addition to any Libraries, frameworks and other constructs.
- Exponential Complexity: With organisations relying on layers of third-party and fourth-party services, the attack surface expands exponentially.
- Insufficient Oversight: Organisations often focus on securing their environments while neglecting the vendors and libraries they depend on.
- Lagging Standards: The industry’s inability to enforce stringent security protocols across the supply chain leaves critical gaps.
- Sophistication of Attacks: From SolarWinds to MOVEit, attackers continually evolve, targeting blind spots in detection and remediation frameworks.
Recommended Steps to Mitigate Supply Chain Threats
To address these vulnerabilities and build resilience, organizations can take the following actionable steps:
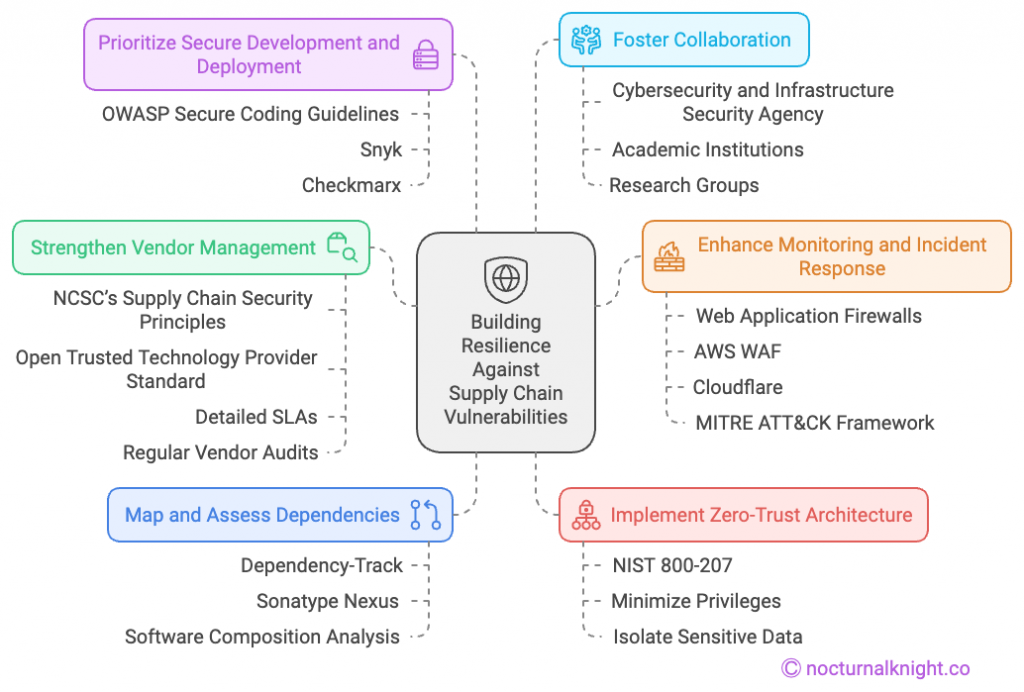
1. Map and Assess Dependencies
- Use tools like Dependency-Track or Sonatype Nexus to map and analyze all third-party and open-source dependencies.
- Regularly perform software composition analysis (SCA) to detect outdated or vulnerable components.
2. Implement Zero-Trust Architecture
- Leverage Zero-Trust frameworks like NIST 800-207 to ensure strict authentication and access controls across all systems.
- Minimize the privileges of third-party integrations and isolate sensitive data wherever possible.
3. Strengthen Vendor Management
- Evaluate vendor security practices using frameworks like the NCSC’s Supply Chain Security Principles or the Open Trusted Technology Provider Standard (OTTPS).
- Demand transparency through detailed Service Level Agreements (SLAs) and regular vendor audits.
4. Prioritize Secure Development and Deployment
- Train your development teams to follow secure coding practices like those outlined in the OWASP Secure Coding Guidelines.
- Incorporate tools like Snyk or Checkmarx to identify vulnerabilities during the software development lifecycle.
5. Enhance Monitoring and Incident Response
- Deploy Web Application Firewalls (WAFs) such as AWS WAF or Cloudflare to protect web interfaces.
- Establish a robust incident response plan using guidance from the MITRE ATT&CK Framework to ensure rapid containment and mitigation.
6. Foster Collaboration
- Work with industry peers and organizations like the Cybersecurity and Infrastructure Security Agency (CISA) to share intelligence and best practices for supply chain security.
- Collaborate with academic institutions and research groups for cutting-edge insights into emerging threats.
7. Schedule a No-Obligation Consultation Call with Yours Truly
Struggling with supply chain vulnerabilities or need tailored solutions for your unique challenges? I offer consultation services to work directly with your CTO, Principal Architect, or Security Leadership team to:
- Assess your systems and identify key risks.
- Recommend actionable, budget-friendly steps for mitigation and prevention.
With years of expertise in cybersecurity and compliance, I can help streamline your approach to supply chain security without breaking the bank. Let’s collaborate to make your operations secure and resilient.
Schedule Your Free Consultation Today
Building a Resilient Supply Chain
The UK’s National Cyber Security Centre (NCSC) principles for supply chain security provide a pragmatic roadmap for businesses. Here’s how to act:
- Understand and Map Dependencies
Organizations should create a detailed map of all dependencies, including direct vendors and downstream providers, to identify potential weak links. - Adopt a Zero-Trust Framework
Treat every external connection as untrusted until verified, with continuous monitoring and access restrictions. - Mandate Secure Development Practices
Encourage or require vendors to implement secure coding standards, frequent vulnerability testing, and robust update mechanisms. - Regularly Audit Supply Chains
Establish a routine audit process to assess vendor security posture and adherence to compliance requirements. - Proactive Incident Response Planning
Prepare for the inevitable by maintaining a robust incident response plan that incorporates supply chain risks.
Final Thoughts
The threat of supply chain vulnerabilities is no longer hypothetical—it’s happening now. With reports like CyCognito’s, research into dependency management, and frameworks provided by trusted institutions, businesses have the tools to mitigate risks. However, this requires vigilance, collaboration, and a willingness to rethink traditional approaches to third-party management.
Organisations must act not only to safeguard their operations but also to preserve trust in an increasingly interconnected world.
Is your supply chain ready to withstand the next wave of attacks?
References and Further Reading
- Report Shows the Threat of Supply Chain Vulnerabilities from Third-Party Products – CyCognito
- Hidden Threats in PyPI and NPM: What You Need to Know
- Why Software Supply Chain Attacks Persist – Scientific Computing World
- Principles of Supply Chain Security – NCSC
- CyCognito Report Exposes Rising Software Supply Chain Threats
What’s your strategy for managing third-party risks? Share your thoughts in the comments!