Scattered Spider Attacks: Tips for SaaS Security

As cloud adoption soars, threat groups like LUCR-3 Scattered Spider and Oktapus are mastering new ways to exploit identity management systems(IAMs), making these attacks more frequent and harder to detect. By targeting cloud environments and leveraging human vulnerabilities, LUCR-3 compromises identity providers (IDPs) and uses sophisticated techniques to breach organizations.
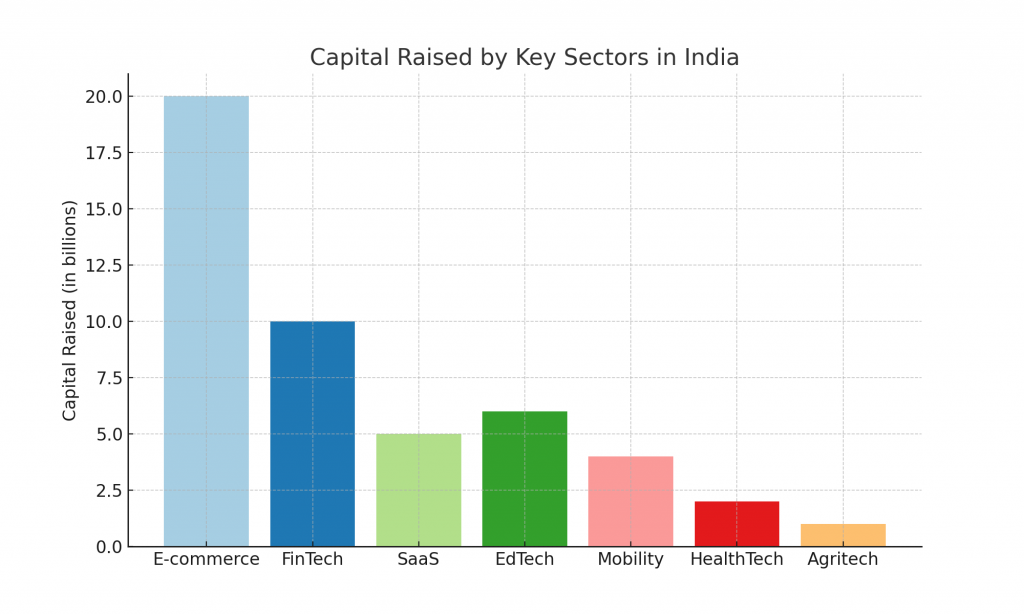
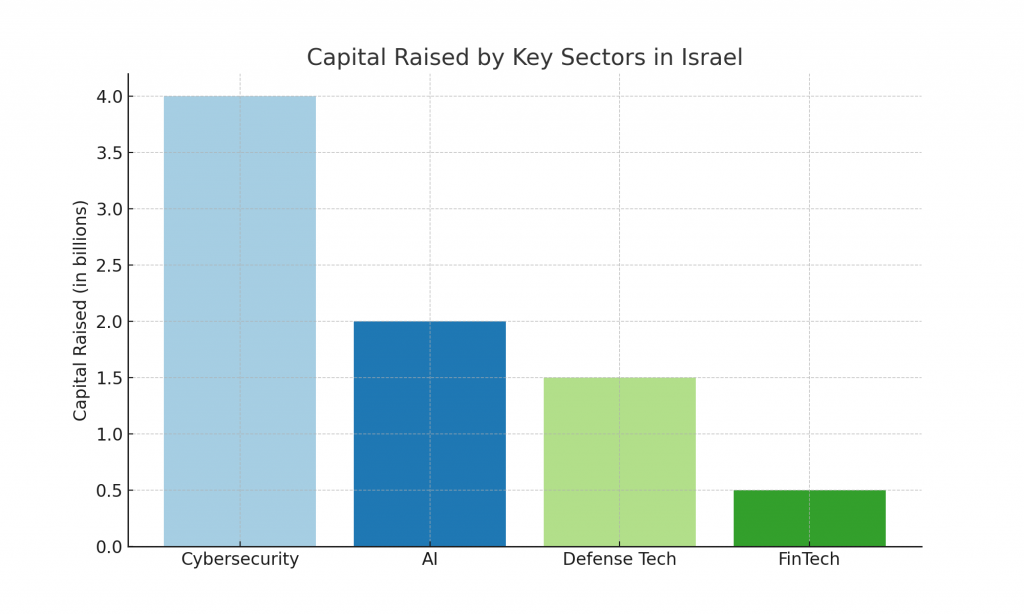
Before we begin, I wanted to present a random sampling of the successful attacks carried over by the LUCR-3 aka Scattered Spider.
| Company/Product | Date Attacked | Compromised System | Projected Loss | Mitigation Time |
|---|---|---|---|---|
| Telecom Company (Unnamed) | December 2022 | Mobile Carrier Network, IDP Systems | Estimated millions in damages | Several weeks (ongoing)CrowdStrike |
| Octa (Roasted Oktapus) | March 2022 | Identity Provider (Okta) and SaaS | Potential damage to ~366 companies | 4-5 weeksHeroWikipedia |
| British Telecommunications | June 2022 | Mobile Carrier Systems, BPO Networks | Millions in lost revenue | 3-4 weeksCrowdStrikeHero |
| Gaming Company (Unnamed) | September 2022 | Cloud Infrastructure (SaaS and IaaS) | Losses in IP theft (unconfirmed) | ~2 weeksISPM ITDR |
| Cloud Hosting Provider | November 2022 | AWS, Azure Environments, IAM Systems | IP theft and reputational damage | 3 weeksCrowdStrike |
| MGM Resorts | September 2023 | Corporate systems, Help Desk, and IDP | Millions in lost revenue | Systems offline for weeksWikipedia |
| Caesars Entertainment | September 2023 | Identity Providers (IDP) and SaaS | ~$30 million ransom paid Wikipedia | ~1 month recoveryCyber Defense Magazine |
| Charter Communications | April 2024 | Cloud-based systems (Okta phishing) | Potentially millions in damages Resilience | Several weeks |
| NHS Hospitals (UK) | June 2024 | VMware ESXi servers, critical healthcare systems | Disruption of hundreds of operationsBleepingComputer | OngoingBleepingComputer |
| Synnovis Pathology Services | June 2024 | Ransomware on pathology services systems | Estimated millions in healthcare disruptionsBleepingComputer | Ongoing investigationBleepingComputer |
This article outlines the technical steps LUCR-3 typically follows, from initial access to persistence and lateral movement within cloud environments, mostly targeting SaaS platforms.
Step 1: Initial Access Through Identity Compromise
LUCR-3 starts with a core weakness in modern security—identity management. Their main attack vectors include:
- SIM Swapping: LUCR-3 hijacks a user’s phone number by tricking the telecom provider into assigning the number to a new SIM card. Once they have control over the phone number, they can intercept One-Time Passwords (OTP) sent via SMS.
- MFA Fatigue: The attackers flood the target with repeated MFA prompts, often overwhelming them into approving a malicious login request.
- Phishing and Social Engineering: They set up fake login pages for SaaS applications (e.g., SharePoint or OneDrive), capturing legitimate credentials and OTP codes.
These techniques allow LUCR-3 to bypass standard Multi-Factor Authentication (MFA) protections and gain access to cloud environments
Step 2: Bypassing MFA and Establishing a Foothold
Once inside, LUCR-3 focuses on maintaining access to the compromised identity. This is done by modifying the victim’s MFA settings. Their tactics include:
- Registering New Devices: LUCR-3 will register their own devices (phones or emails) under the victim’s account, which ensures they can log in without triggering alerts. For example, they might register an iPhone if the victim previously used Android, raising minimal suspicion.
- Adding Alternate MFA Methods: They add backup MFA methods, such as an external email address, making it even harder to lock them out if the breach is discoveredISPM ITDR.
Step 3: Reconnaissance and Data Collection in SaaS Environments
After gaining access to cloud platforms, LUCR-3 conducts extensive reconnaissance to identify critical assets, credentials, and sensitive information. Here’s how they do it:
- SaaS Platforms: They use native tools within platforms like SharePoint, OneDrive, and Salesforce to search for documents containing passwords, intellectual property, or financial data. They operate like legitimate users to avoid detection.
- AWS Cloud: In AWS environments, LUCR-3 navigates the AWS Management Console, targeting services like EC2 (Elastic Compute Cloud) and S3 (Simple Storage Service). They leverage the AWS-GatherSoftwareInventory job through Systems Manager (SSM) to list running software across EC2 instances ISPM ITDR.
- Privilege Escalation: LUCR-3 may modify IAM roles or escalate privileges by updating LoginProfiles or creating new access keys, ensuring they have continued administrative accessHero.
Step 4: Lateral Movement and Persistence
LUCR-3 ensures they have multiple ways to re-enter a compromised environment, even if one of their entry points is discovered. Here’s how they achieve persistence:
- Create New IAM Users: LUCR-3 creates new user accounts that align with the naming conventions of the compromised environment to avoid suspicion. These accounts often have high-level access, allowing them to continue accessing the environment even after the initial breach is patched.
- Secrets Harvesting: Using tools like S3 Browser, LUCR-3 harvests credentials stored in AWS Secrets Manager and similar services, allowing them to steal sensitive data and further penetrate systems Hero.
- MFA Manipulation: They alter MFA settings to ensure continued access, often registering additional email addresses or devices that align with the compromised identity.
Step 5: Data Exfiltration and Extortion
Once LUCR-3 has gained the necessary access and gathered sensitive data, they execute their final stage of the attack, which often involves extortion. The data collected during their reconnaissance, such as customer information or proprietary code, is used as leverage to demand payment from the compromised organization The Hacker News ISPM ITDR.
How to Detect and Prevent LUCR-3 Attacks
Given LUCR-3’s sophisticated techniques, organizations must adopt advanced security measures to detect and mitigate such attacks:
- Monitor MFA Changes: Keep a close watch for unusual changes in MFA settings, such as new device registrations or changes from app-based authentication to SMS-based methods.
- Audit Cloud Logs: Regularly audit cloud environments, especially IAM policy changes, new access key creation, and suspicious activity in management consoles.
- Behavioral Anomaly Detection: Implement advanced behavioral monitoring to detect when legitimate accounts are being used in unusual ways, such as accessing unfamiliar services or using unfamiliar devices.
Conclusion
LUCR-3 (Scattered Spider) represents a new breed of cyber threat actors that rely on identity compromise rather than malware or brute force. By targeting the very foundation of security—identity—they can infiltrate cloud environments, move laterally, and exfiltrate data with relative ease. As organizations increasingly rely on cloud services, strengthening identity management, closely monitoring for anomalies, and responding quickly to suspicious behavior are critical defenses against such attacks.
References and Further Reading
- The Hacker News: Provides a detailed breakdown of LUCR-3’s identity-based attacks across cloud environments, lateral movement techniques, and persistence strategies.
- Permiso.io: Discusses how LUCR-3 targets identity infrastructure, modifies MFA settings, and maintains persistence in cloud environments like AWS and Azure.
- CrowdStrike: Offers insights into Scattered Spider’s use of the Bring-Your-Own-Vulnerable-Driver (BYOVD) technique and their focus on telecom and BPO sectors.
- Resilience Cyber Research: Highlights recent phishing campaigns by LUCR-3 in 2024, targeting industries such as telecom, food services, and tech, using Okta-based phishing tactics.
- EclecticIQ: Discusses LUCR-3’s involvement in ransomware attacks targeting cloud infrastructures within the insurance and financial sectors, leveraging smishing and phishing techniques.
- Wikipedia (Scattered Spider): Overview of the MGM Resorts hack in 2023, detailing how Scattered Spider gained access to internal systems through social engineering and caused significant disruptions.
- Cyber Defense Magazine: Discusses how LUCR-3 has highlighted vulnerabilities in MFA and cloud security, predicting more targeted attacks on SaaS and cloud service providers.
- BleepingComputer: Provides an overview of LUCR-3’s collaboration with ransomware groups like Qilin, targeting high-profile companies such as MGM Resorts and healthcare services.
- Caesars and MGM Hacking Incident: Outlines how Caesars Entertainment suffered a breach in September 2023, paying a ~$30 million ransom, while MGM Resorts experienced extensive downtime following a similar attack.
- Microsoft and Qilin Ransomware: Microsoft linked Scattered Spider to ransomware attacks using the Qilin variant, affecting companies like Synnovis Pathology and NHS hospitals in 2024. Read more BleepingComputer Wikipedia
These resources offer in-depth insights into the attack strategies and defence mechanisms relevant to LUCR-3 (Scattered Spider), perfect for anyone looking to deepen their understanding of identity-based attacks and cloud security.