Supply-Chain Extortion Lessons from the Pornhub-Mixpanel Incident
When the Weakest API Becomes the Loudest Breach.
Key Takeaways for Security Leaders
- Extortion is the New Prize: Threat actors like ShinyHunters target behavioral context over credit cards because it offers higher leverage for blackmail.
- The “Zombie Data” Risk: Storing historical analytics from 2021 in 2025 created a massive liability that outlived the vendor contract.
- TPRM Must Be Continuous: Static annual questionnaires cannot detect dynamic shifts in vendor risk or smishing-led credential theft.
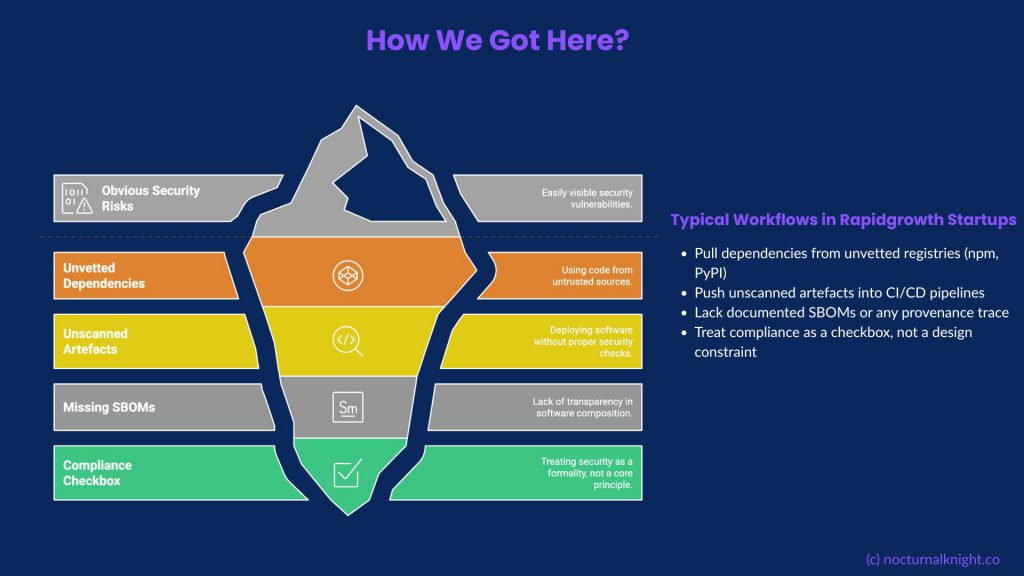
You can giggle about the subject if you want. The headlines almost invite it. An adult platform. Premium users. Leaked “activity data.” It sounds like internet tabloid fodder.
But behind the jokes is a breach that should make every security leader deeply uncomfortable. On November 8, 2025, reports emerged that the threat actor ShinyHunters targeted Mixpanel, a third-party analytics provider used by Pornhub. While the source of the data is disputed, the impact is not: over 200 million records of premium user activity were reportedly put on the auction block.
The entry point? A depressingly familiar SMS phishing (smishing) attack. One compromised credential. One vendor environment breached. The result? Total exposure of historical context.
Not a Data Sale, an Extortion Play
This breach is not about dumping databases on underground forums for quick cash. ShinyHunters are not just selling data; they are weaponizing it through Supply-Chain Extortion.
The threat is explicit: Pay, or sensitive behavioral data gets leaked. This data is valuable not because it contains CVV codes, but because it contains context.
- What users watched.
- When and how often they logged in.
- Patterns of behavior that can be correlated, de-anonymized, and weaponized.
That kind of dataset is gold for sophisticated phishing operations and blackmail campaigns. In 2025, this is no longer theft. This is leverage.
The “Zombie Data” Problem: Risk Outlives Revenue
Pornhub stated they had not worked with Mixpanel since 2021. Legally, this distinction matters. Operationally, it’s irrelevant.
If data from 2021 is still accessible in 2025, you haven’t offboarded the vendor; you’ve just stopped paying the bill while keeping the risk open. This is “Zombie Data”—historical records that linger in third-party environments long after the business value has expired.
Why Traditional TPRM Fails the Extortion Test
Most Third-Party Risk Management (TPRM) programs are static compliance exercises—annual PDFs and point-in-time attestations. This model fails because:
- Risk is Dynamic: A vendor’s security posture can change in the 364 days between audits.
- API Shadows: Data flows often expand without re-scoping the original risk assessment.
- Incomplete Offboarding: Data deletion is usually “assumed” via a contract clause rather than verified via technical evidence.
Questions That Actually Reduce Exposure
If incidents like this are becoming the “new normal,” it is because we are asking the wrong questions. To secure the modern supply chain, leadership must ask:
- Inventory of Flow: Are we continuously aware of what data is flowing to which vendors today—not just at the time of procurement?
- Verification of Purge: Do we treat vendor offboarding as a verifiable security event? (Data deletion should be observable, not just a checked box in an email).
- Contextual Blast Radius: If this vendor is breached, is the data “toxic” enough to fuel an extortion campaign?
You Can Outsource Functions, Not Responsibility
It is tempting to believe that liability clauses will protect your brand. They won’t. When a vendor loses your customer data, your organization pays the reputational price. Your users do not care which API failed, and in 2025, regulators rarely do either.
You can outsource your analytics, your infrastructure, and your speed. But you cannot outsource the accountability for your users’ privacy.
Laugh at the headline if you want. But understand the lesson: The next breach may not come through your front door, it will come through the “trusted” side door you forgot to lock years ago.