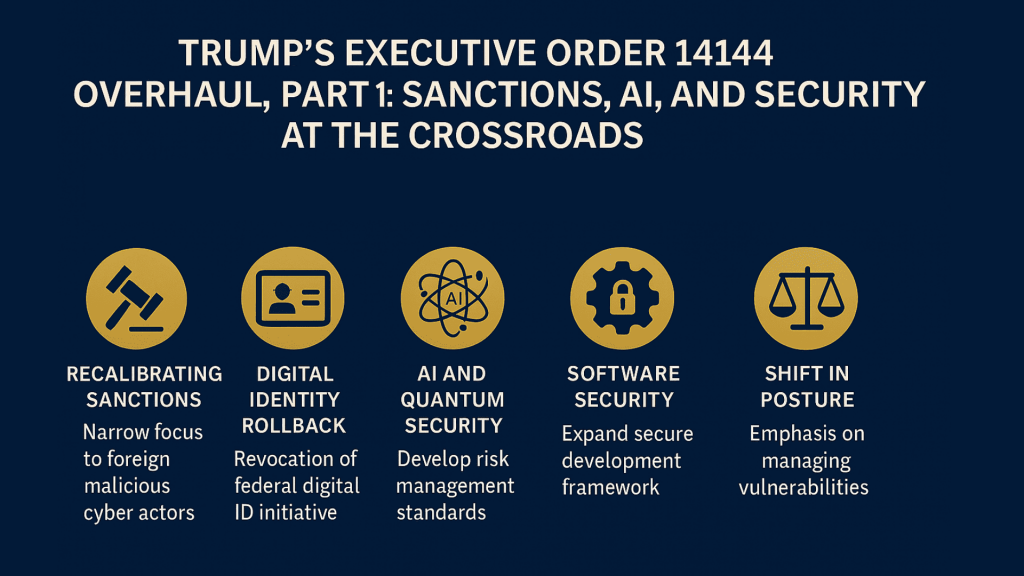
Trump’s Executive Order 14144 Overhaul, Part 2: Analysis of Post Quantum Cryptography Clauses
While Part 1 explored how the amendment reinforced a sanctions-led approach and repositioned AI policy within the broader cybersecurity doctrine, this second instalment shifts focus to its most understated move — the cryptographic recalibration. Executive Order 14144’s treatment of Post-Quantum Cryptography (PQC) may appear procedural at first glance, but in its omissions and realignments lies a deeper signal about how the United States intends to balance resilience, readiness, and sovereignty in a quantum-threatened world.
Executive Summary
The June 2025 amendment to Executive Order 14144 quietly redefines the United States’ approach to Post-Quantum Cryptography (PQC). While it retains the recognition of CRQC as a threat and maintains certain tactical mandates such as TLS 1.3, it rolls back critical enforcement mechanisms and abandons global coordination. This signals a strategic recalibration, shifting from enforced transition to selective readiness. For enterprise CISOs, vendors, and cybersecurity strategists, the message is clear: leadership on PQC will now emerge from the ground up.
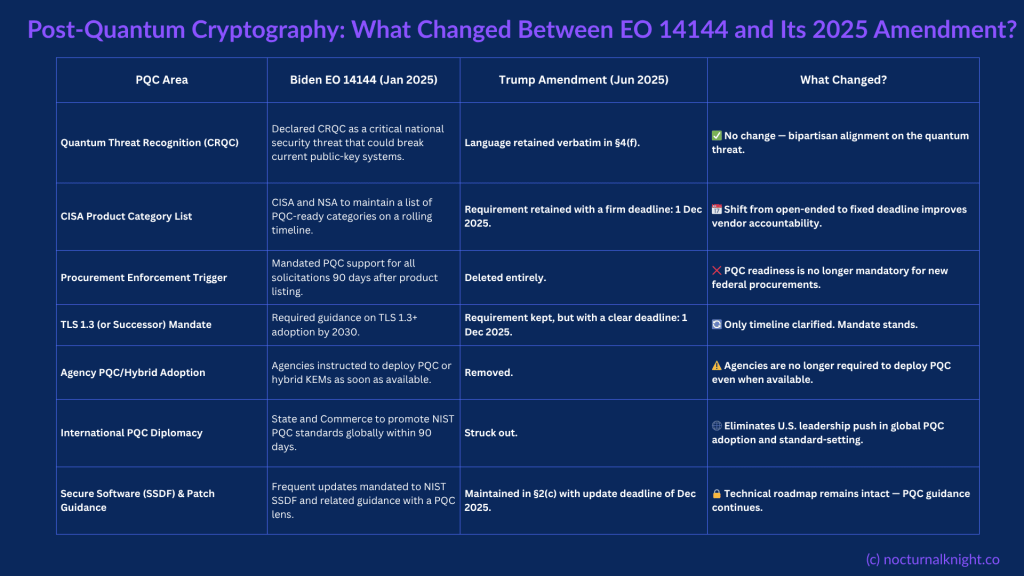
What the Amendment Changed
The Trump administration’s June 2025 revision to EO 14144 leaves much of the cryptographic threat framing intact, but systematically reduces deployment timelines and global mandates. Notably:
- CRQC remains listed as a critical national threat
- TLS 1.3 mandate remains, now with clarified deadlines
- SSDF and patching guidance are retained
- The CISA product list deadline is upheld
However, three key changes undermine its enforceability:
- The 90-day procurement trigger for PQC tools is removed
- Agencies are no longer required to deploy PQC when available
- The international coordination clause promoting NIST PQC globally is eliminated
Why the International Clause Matters
The removal of the global coordination clause is more than a bureaucratic adjustment; it represents a strategic shift.
Possible Reasons:
- Geopolitical pragmatism: Aligning allies behind NIST PQC may be unrealistic with Europe pursuing crypto-sovereignty and China promoting SM2
- Avoiding early lock-in: Promoting PQC globally before commercial maturity risks advocating immature technologies
- Supply chain nationalism: This may be a move to protect the domestic PQC ecosystem from premature exposure or standards capture
- Sanctions-first strategy: The EO prioritises the preservation of cyber sanctions infrastructure, signalling a move from soft power (standards promotion) to hard deterrence
This aligns with the broader tone of the EO amendment, consolidating national tools while reducing forward-facing mandates.
From Mandate to Optionality: PQC Enforcement Rolled Back
The deletion of the PQC procurement requirement and deployment enforcement transforms the United States’ posture from proactive to reactive. There is no longer a mandate that agencies or vendors use post-quantum encryption; instead, it encourages awareness.
This introduces several risks:
- Agencies may delay PQC adoption while awaiting further guidance
- Vendors face uncertainty, questioning whether to prepare for future mandates or focus on current market readiness
- Federal supply chains may remain vulnerable well into the 2030s
Strategic Implications: A Doctrine of Selective Resilience
This amendment reflects a broader trend: preserving the appearance of resilience without committing to costly transitions. It signifies:
- A shift towards agency-level discretion over central enforcement
- A belief that commercial readiness should precede policy enforcement
- A pivot from global cyber diplomacy to domestic cyber deterrence
This is not a retreat, it is a repositioning.
What Enterprises and Vendors Should Do Now
Despite the rollback, the urgency surrounding PQC remains. Forward-thinking organisations should:
- Inventory vulnerable cryptographic systems such as RSA and ECC
- Introduce crypto-agility frameworks to support seamless algorithm transitions
- Explore hybrid encryption schemes that combine classical and quantum-safe algorithms
- Monitor NIST, NSA (CNSA 2.0), and OMB guidance closely
For vendors, supporting PQC and crypto-agility will soon become a market differentiator rather than merely a compliance requirement.
Conclusion: Optionality is Not Immunity
The Trump EO amendment does not deny the quantum threat. It simply refrains from mandating early adoption. This increases the importance of voluntary leadership. Those who embed quantum-resilient architectures today will become the trust anchors of the future.
Optionality may offer policy flexibility, but it does not eliminate risk.