Oracle Cloud Breach Is a Transitive Trust Timebomb : Here’s How to Defuse It
“One mispatched server in the cloud can ignite a wildfire of trust collapse across 140,000 tenants.”
1. The Context: Why This Matters
In March 2025, a breach at Oracle Cloud shook the enterprise SaaS world. A few hours after Rahul from CloudSEK first flagged signs of a possible compromise, I published an initial analysis titled Is Oracle Cloud Safe? Data Breach Allegations and What You Need to Do Now. That piece was an urgent response to a fast-moving situation, but this article is the reflective follow-up. Here, I break down not just the facts of what happened, but the deeper problem it reveals: the fragility of transitive trust in modern cloud ecosystems.
Threat actor rose87168 leaked nearly 6 million records tied to Oracle’s login infrastructure, affecting over 140,000 tenants. The source? A misconfigured legacy server still running an unpatched version of Oracle Access Manager (OAM) vulnerable to CVE‑2021‑35587.
Initially dismissed by Oracle as isolated and obsolete, the breach was later confirmed via datasets and a tampered page on the login domain itself, captured in archived snapshots. This breach was not just an Oracle problem. It was a supply chain problem. The moment authentication breaks upstream, every SaaS product, platform, and identity provider depending on it inherits the risk, often unknowingly.
Welcome to the age of transitive trust. shook the enterprise SaaS world. Threat actor rose87168 leaked nearly 6 million records tied to Oracle’s login infrastructure, affecting over 140,000 tenants. The source? A misconfigured legacy server still running an unpatched version of Oracle Access Manager (OAM) vulnerable to CVE‑2021‑35587.
Initially dismissed by Oracle as isolated and obsolete, the breach was later confirmed via datasets and a tampered page on the login domain itself, captured in archived snapshots. This breach was not just an Oracle problem. It was a supply chain problem. The moment authentication breaks upstream, every SaaS product, platform, and identity provider depending on it inherits the risk, often unknowingly.
Welcome to the age of transitive trust.
2. Anatomy of the Attack
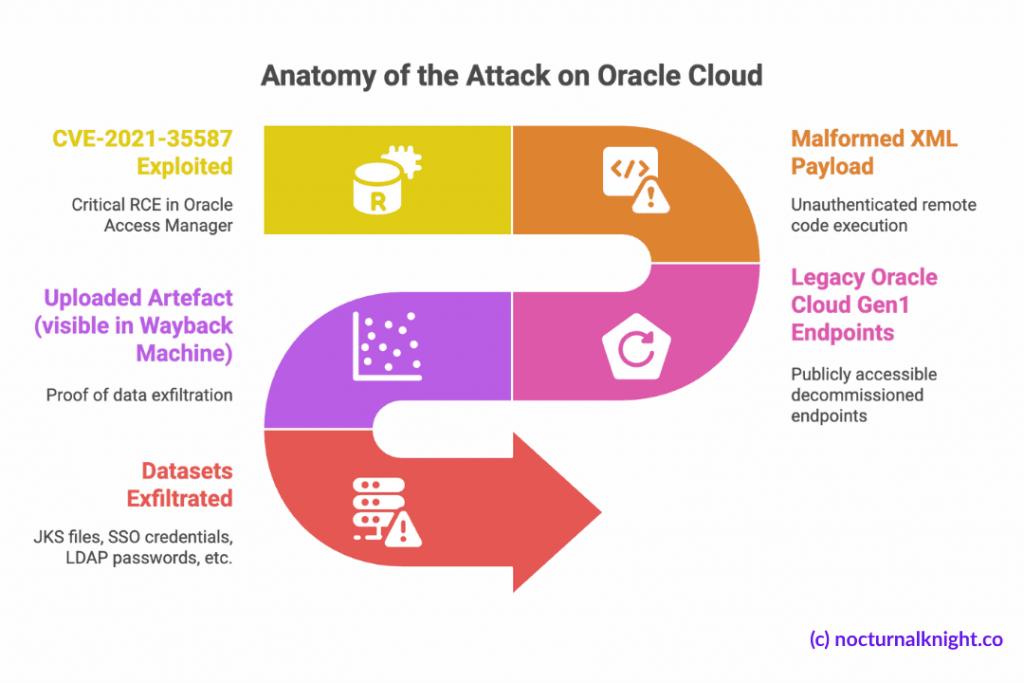
Attack Vector
- Exploited: CVE-2021-35587, a critical RCE in Oracle Access Manager.
- Payload: Malformed XML allowed unauthenticated remote code execution.
Exploited Asset
- Legacy Oracle Cloud Gen1 login endpoints still active (e.g.,
login.us2.oraclecloud.com). - These endpoints were supposedly decommissioned but remained publicly accessible.
Proof & Exfiltration
- Uploaded artefact visible in Wayback Machine snapshots.
- Datasets included:
- JKS files, encrypted SSO credentials, LDAP passwords
- Tenant metadata, PII, hashes of admin credentials
Validated by researchers from CloudSEK, ZenoX, and GoSecure.
3. How Was This Possible?
- Infrastructure drift: Legacy systems like Gen1 login were never fully decommissioned.
- Patch blindness: CVE‑2021‑35587 was disclosed in 2021 but remained exploitable.
- Trust misplacement: Downstream services assumed the upstream IDP layer was hardened.
- Lack of dependency mapping: Tenants had no visibility into Oracle’s internal infra state.
4. How This Could Have Been Prevented
| Oracle’s Prevention Gaps | |
| Vector | Preventive Control |
| Legacy exposure | Enforce infra retirement workflows. Remove public DNS entries for deprecated endpoints. |
| Patch gaps | Automate CVE patch enforcement across cloud services with SLA tracking. |
| IDP isolation | Decouple prod identity from test/staging legacy infra. Enforce strict perimeter controls. |
| What Clients Could Have Done | |
| Risk Inherited | Mitigation Strategy |
| Blind transitive trust | Maintain a real-time trust graph between IDPs, SaaS apps, and their dependencies. |
| Credential overreach | Use scoped tokens, auto-expire shared secrets, enforce rotation. |
| Detection lag | Monitor downstream for leaked credentials or unusual login flows tied to upstream IDPs. |
5. Your Response Plan for Upstream IDP Risk
| Domain | Best Practices |
| Identity & Access | Enforce federated MFA, short-lived sessions, conditional access rules |
| Secrets Management | Store all secrets in a vault, rotate frequently, avoid static tokens |
| Vulnerability Hygiene | Integrate CVE scanners into CI/CD pipelines and runtime checks |
| Visibility & Auditing | Maintain structured logs of identity provider access and token usage |
| Trust Graph Mapping | Actively map third-party IDP integrations, revalidate quarterly |
6. Tools That Help You Defuse Transitive Trust Risks
| Tool | Mitigates | Use Case |
| CloudSEK XVigil | Credential leaks | Monitor for exposure of tokens, admin hashes, or internal credentials in open channels |
| Cortex Xpanse / Censys | Legacy infra exposure | Surface forgotten login domains and misconfigured IDP endpoints |
| OPA / OSQuery / Falco | Policy enforcement | Detect violations of login logic, elevated access, or fallback misroutes |
| Orca / Wiz | Runtime posture | Spot residual access paths and configuration drifts post-incident |
| Sigstore / Cosign | Supply chain integrity | Protect CI/CD artefacts but limited in identity-layer breach contexts |
| Vault (HashiCorp) | Secrets lifecycle | Automate token expiration, key rotation, and zero plaintext exposure |
| Zerberus.ai Trace-AI | Transitive trust, IDP visibility | Discover hidden dependencies in SaaS trust chains and enforce control validation |
7. Lessons Learned
When I sat down to write this, these statements felt too obvious to be called lessons. Of course authentication is production infrastructure, any practitioner would agree. But then why do so few treat it that way? Why don’t we build failovers for our SSO? Why is trust still assumed, rather than validated?
These aren’t revelations. They’re reminders; hard-earned ones.
- Transitive trust is NOT NEUTRAL, it’s a silent threat multiplier. It embeds risk invisibly into every integration.
- Legacy infrastructure never retires itself. If it’s still reachable, it’s exploitable.
- Authentication systems deserve production-level fault tolerance. Build them like you’d build your API or Payment Gateway.
- Trust is not a diagram to revisit once a year; it must be observable, enforced, and continuously verified.
8. Making the Invisible Visible: Why We Built Zerberus
Transitive trust is invisible until it fails. Most teams don’t realise how many of their security guarantees hinge on external identity providers, third-party SaaS integrations, and cloud-native IAM misconfigurations.
At Zerberus, we set out to answer a hard question: What if you could see the trust relationships before they became a risk?
- We map your entire trust graph, from identity providers and cloud resources to downstream tools and cross-SaaS entitlements.
- We continuously verify the health and configuration of your identity and access layers, including:
- MFA enforcement
- Secret expiration windows
- IDP endpoint exposure
- We bridge compliance and security by treating auth controls and access posture as observable artefacts, not static assumptions.
Your biggest security risk may not be inside your codebase, but outside your control plane. Zerberus is your lens into that blind spot.
Further Reading & References
- NocturnalKnight – Is Oracle Cloud Safe? Data Breach Allegations and What You Need to Do Now: https://nocturnalknight.co/is-oracle-cloud-safe-data-breach-allegations-and-what-you-need-to-do-now
- CloudSEK Blog – Oracle Cloud Breach Analysis (2025): https://cloudsek.com/blog/the-biggest-supply-chain-hack-of-2025-6m-records-for-sale-exfiltrated-from-oracle-cloud-affecting-over-140k-tenants
- ZenoX Security – Oracle Leak Sample Validation: https://zenox.ai/en/new-data-from-the-oracle-incident-analysis-and-validation-of-the-10k-line-sample-from-the-reported-leak
- GoSecure – Strategic IDP Exposure Risks: https://gosecure.ai/blog/2025/03/24/oracle-cloud-breach-a-strategic-response-to-an-identity-layer-threat
- Trustwave SpiderLabs – Threat Review: Oracle Access Exploits: https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/trustwave-spiderlabs-threat-review-alleged-oracle-compromise
- Dark Reading – Oracle Denial and Disclosure Timeline: https://www.darkreading.com/cyberattacks-data-breaches/oracle-breach-2-obsolete-servers
- Orca Security – CVE-2021-35587 and Cloud Drift: https://orca.security/resources/blog/oracle-cloud-breach-exploiting-cve-2021-35587
Want to Know Who You’re Really Trusting?
Start your free Zerberus trial and discover the trust graph behind your SaaS stack—before someone else does.

